diff --git a/docs/hub/_toctree.yml b/docs/hub/_toctree.yml
index dce951909..181219e32 100644
--- a/docs/hub/_toctree.yml
+++ b/docs/hub/_toctree.yml
@@ -283,6 +283,8 @@
title: How to configure OIDC with Okta in the Hub
- local: security-sso-okta-saml
title: How to configure SAML with Okta in the Hub
+ - local: security-sso-azure-saml
+ title: How to configure SAML with Azure in the Hub
- local: security-malware
title: Malware Scanning
- local: security-pickle
diff --git a/docs/hub/security-sso-azure-saml.md b/docs/hub/security-sso-azure-saml.md
new file mode 100644
index 000000000..1237171b7
--- /dev/null
+++ b/docs/hub/security-sso-azure-saml.md
@@ -0,0 +1,117 @@
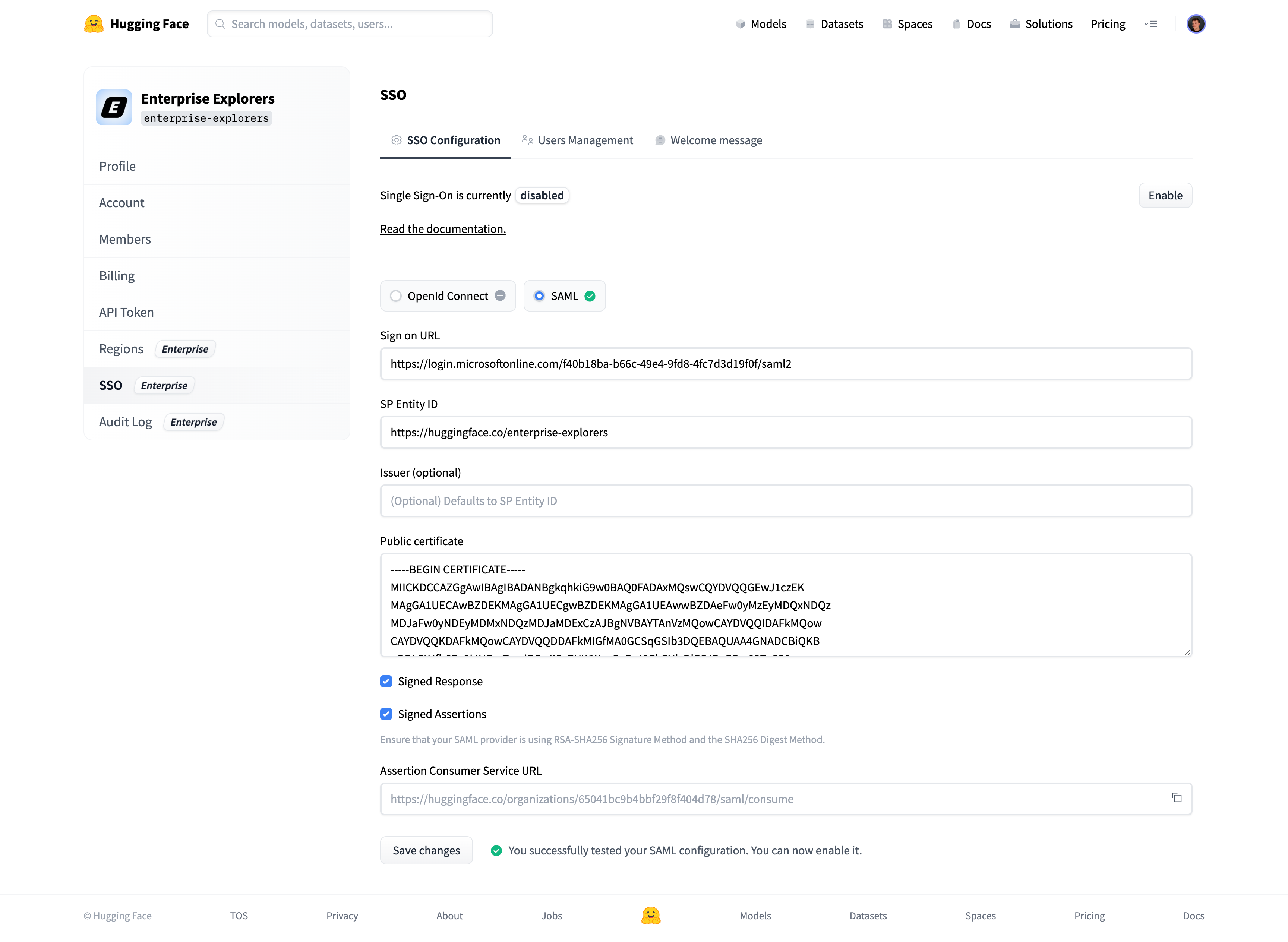
+# How to configure SAML SSO with Azure
+
+In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+
+We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.
+
+
+ This feature is part of the Enterprise Hub.
+
+
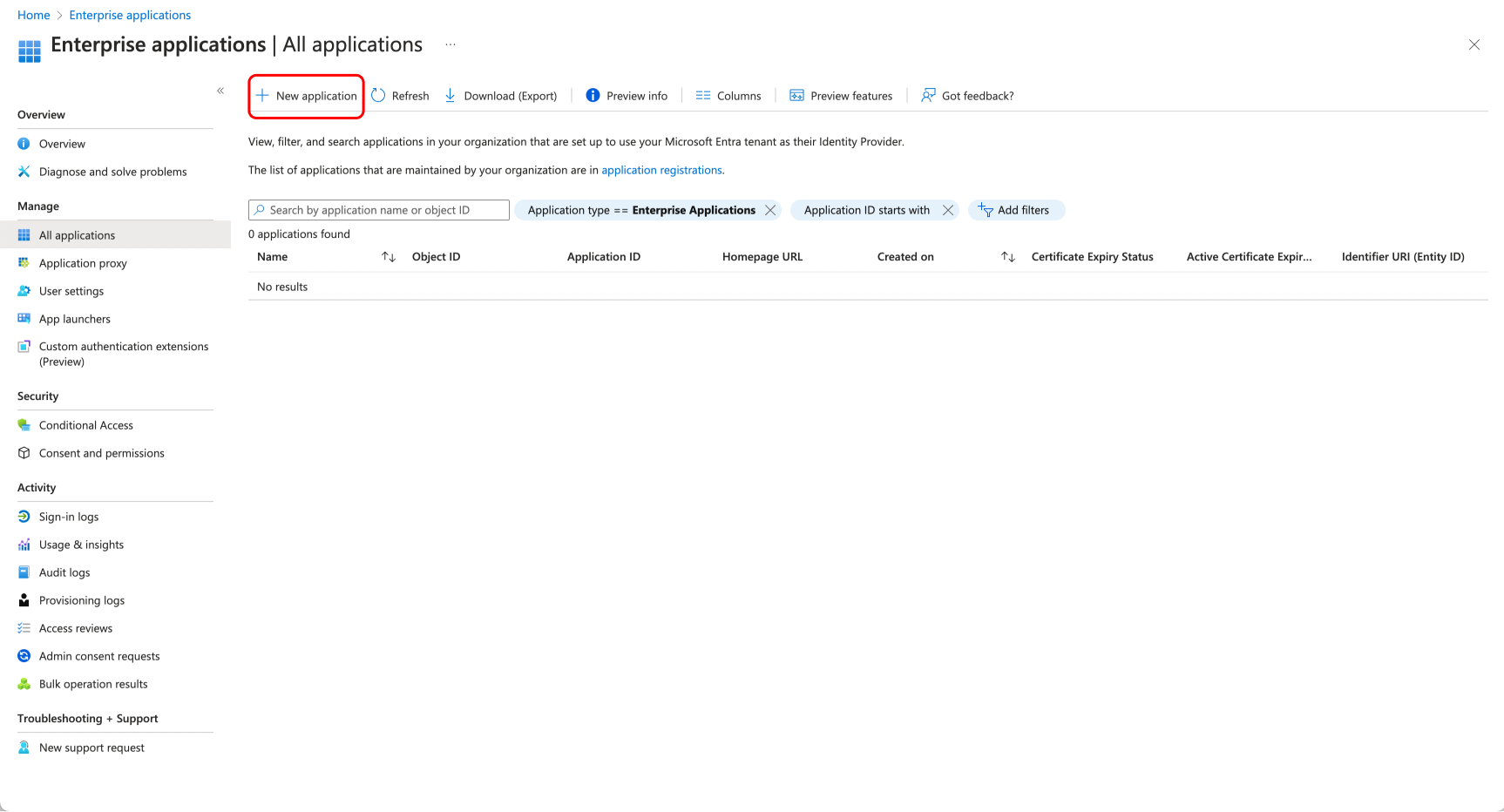
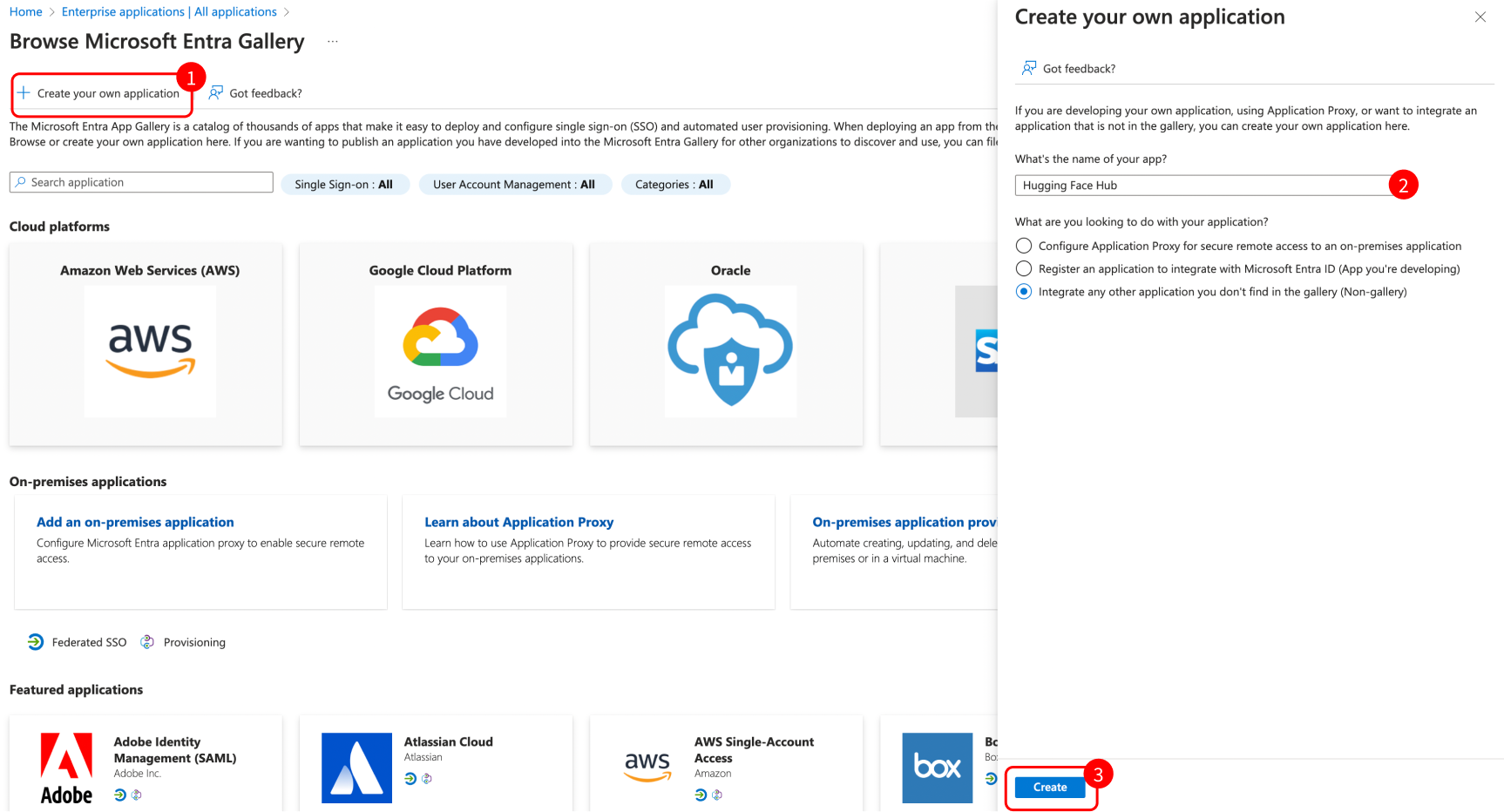
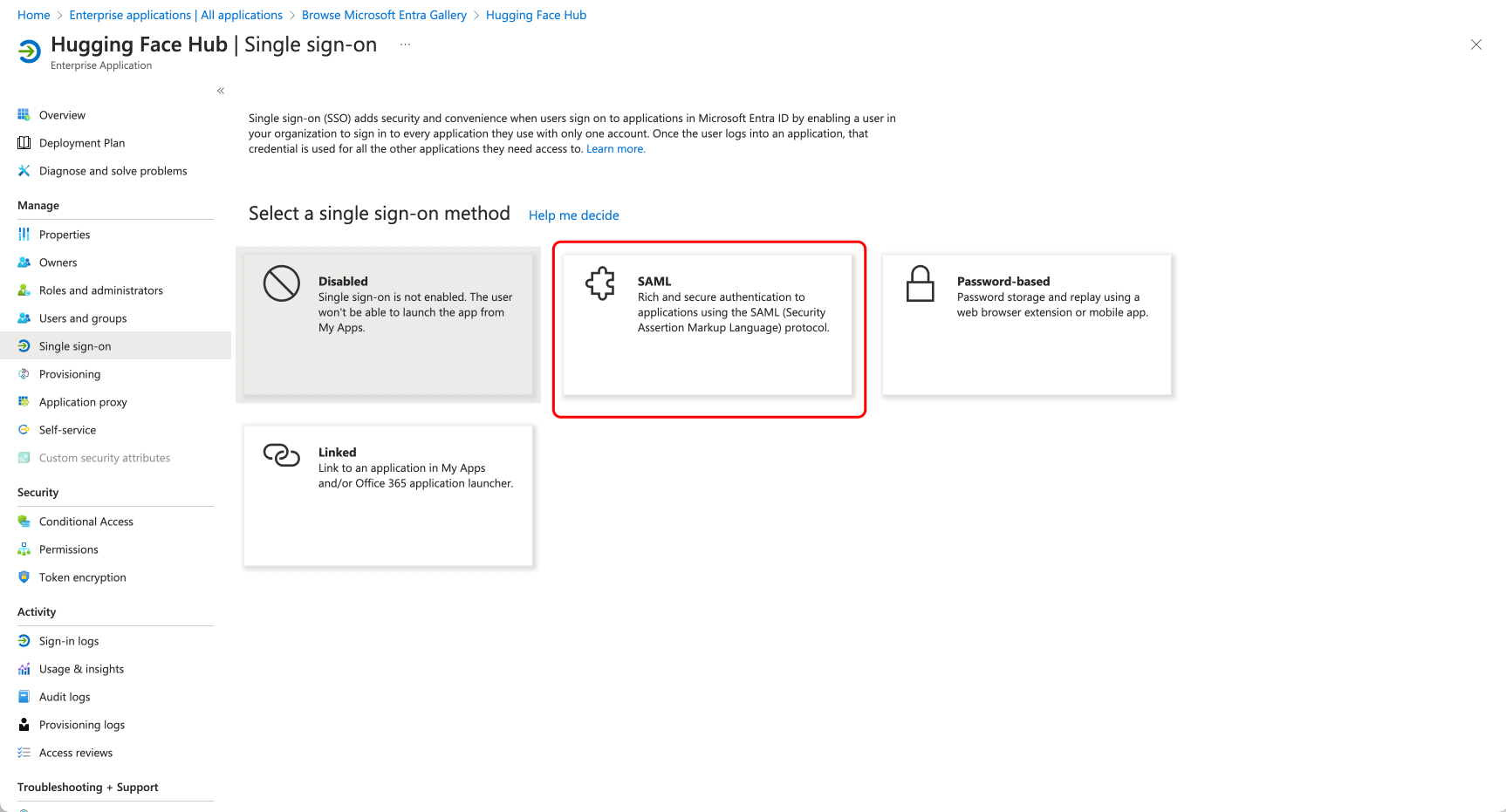
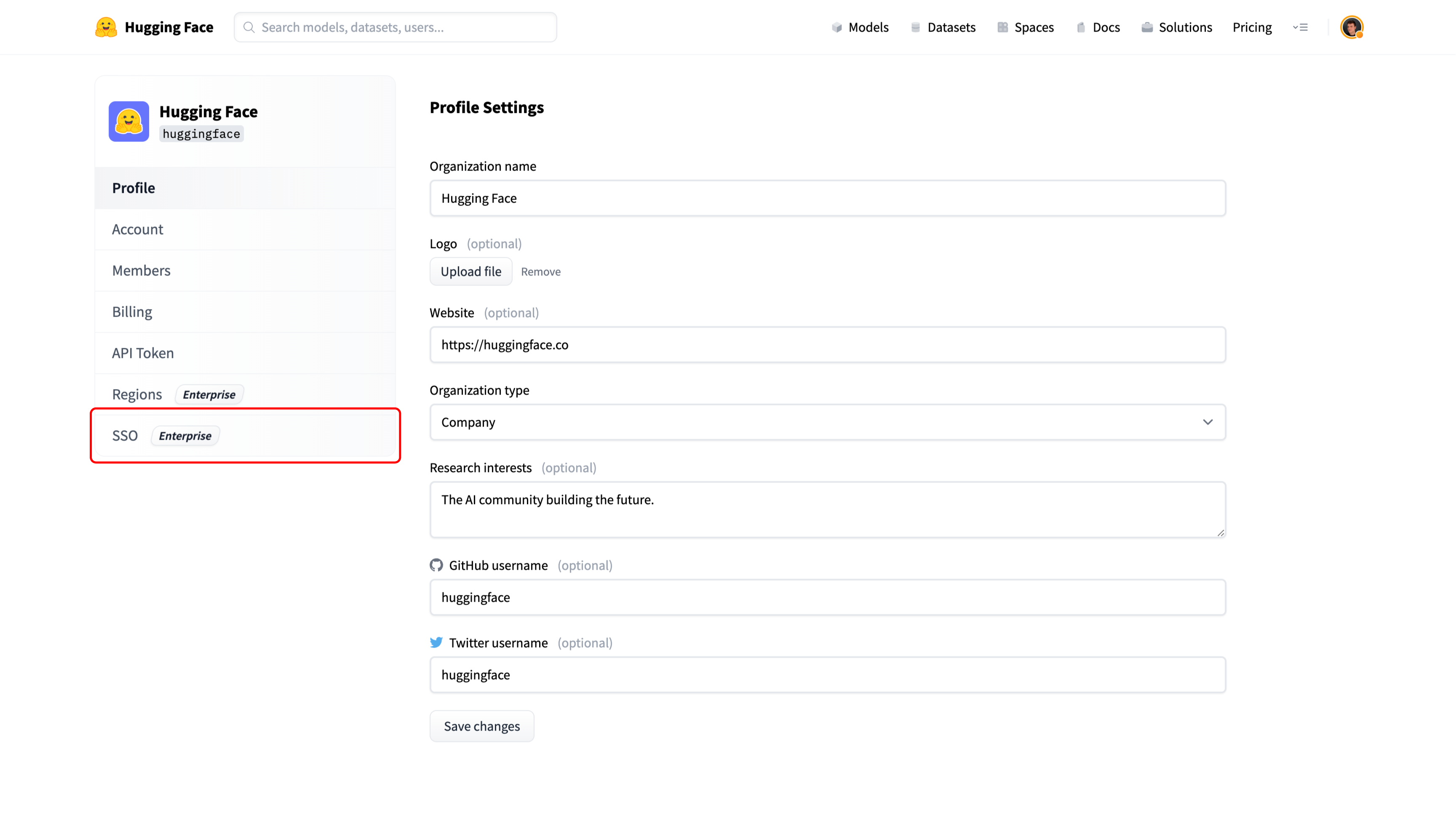
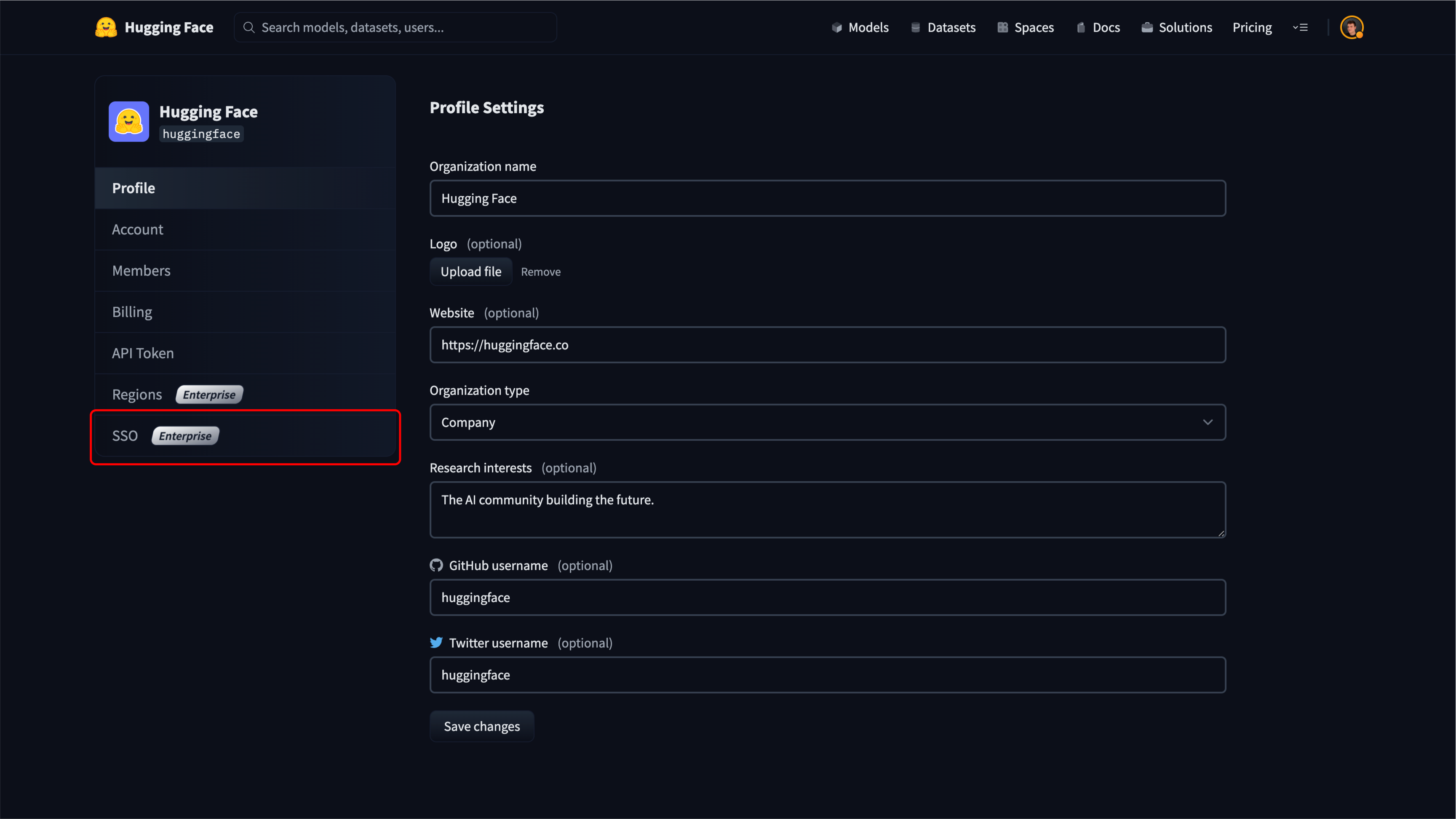
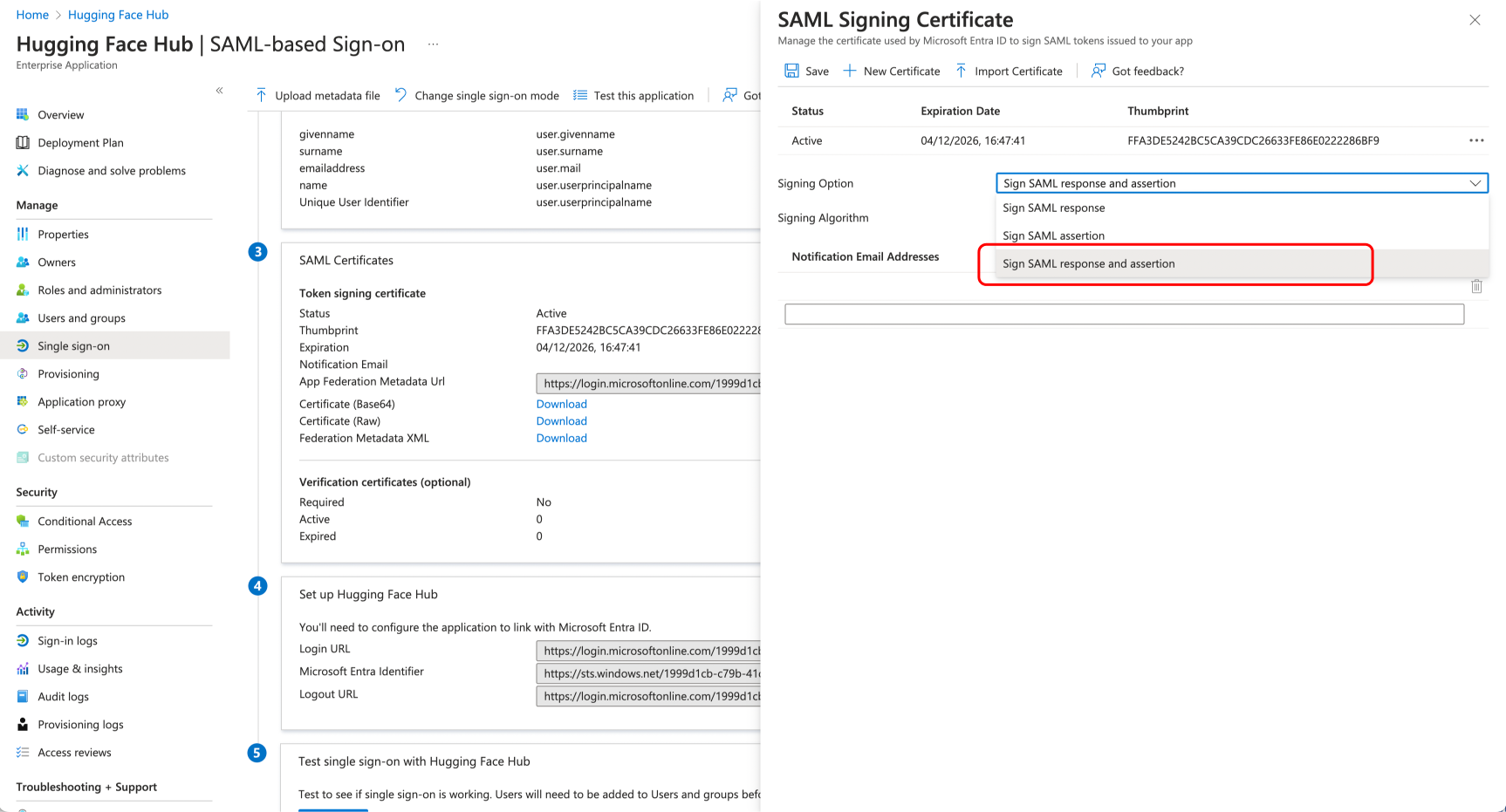
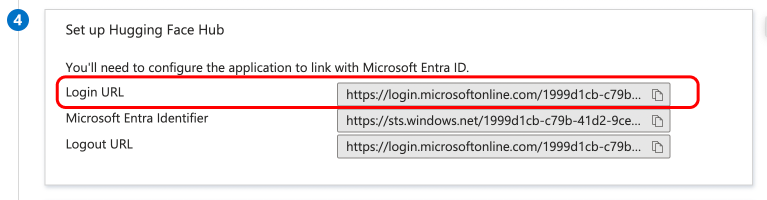
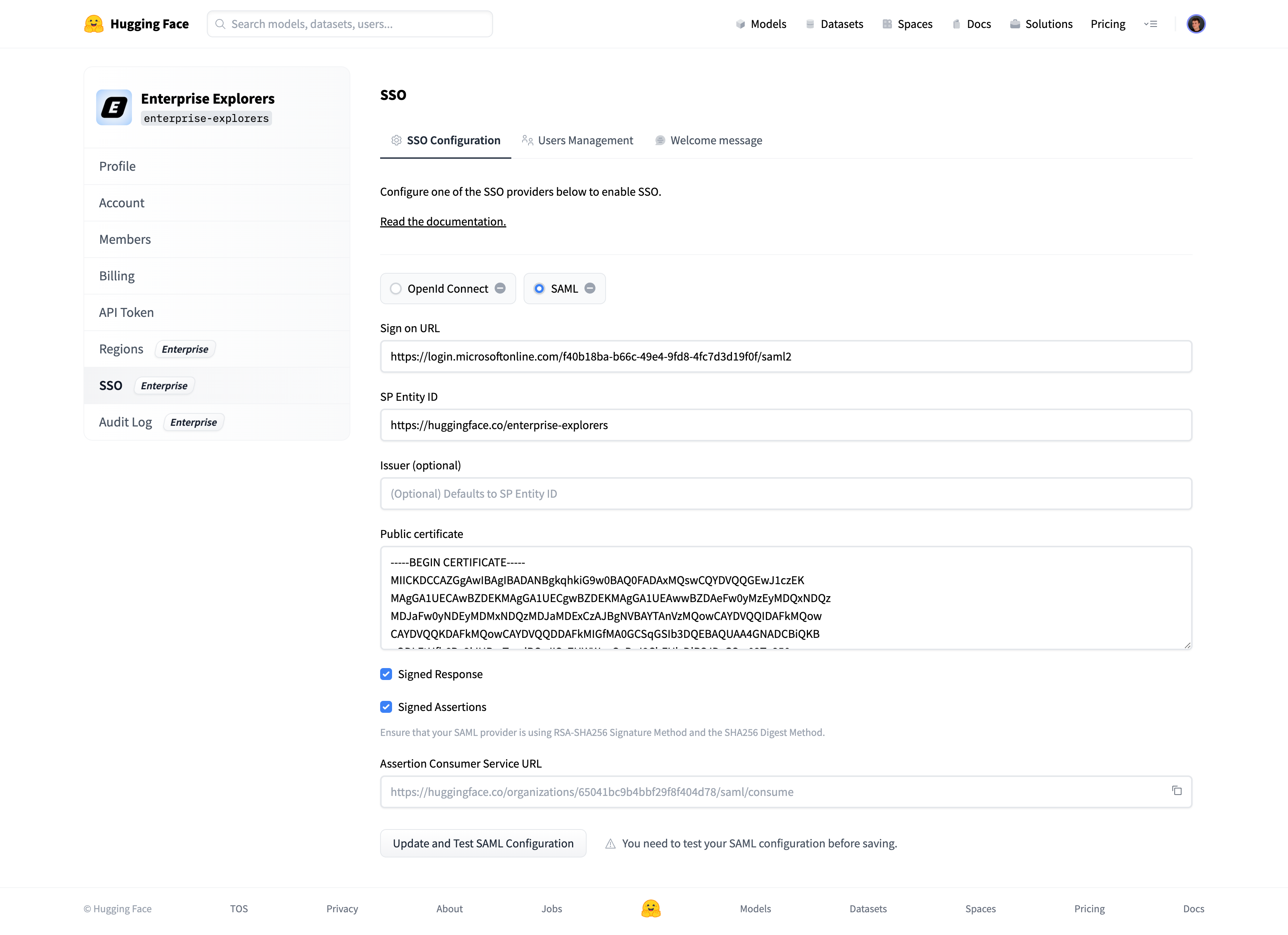
+### Step 1: Create a new application in your Identity Provider
+
+Open a new tab/window in your browser and sign in to the Azure portal of your organization.
+
+Navigate to "Enterprise applications" and click the "New application" button.
+
+
+
+
+
+
+
+
+
+
+
+

+

+
+

+
+
+
+
+
+
+

+
+
+

+
 +
+ +
+ +
+ +
+ +
+ +
+ +
+ +
+ +
+ +
+ +
+ +
+ +
+ +
+  +
+